There’s a good chance that your company is among the 83% of businesses that run the danger of experiencing a data breach. As the data grows, you know your technology assets and systems are at high risk of cyberattacks that cause data breaches. If cybersecurity practices are neglected, this risk becomes much higher.
Now think of the human virome. If we learn to control the harmful viruses in our bodies, we can develop into more powerful organisms. The same applies to your IT infrastructure security. You can rid your business of any cyber threat that infects every part of it like a virus if you know how to take care of your company’s immune system. A solid cybersecurity strategy is your means of preventing unauthorized access to your systems.
What is IT infrastructure security?
IT infrastructure security is the way to effectively protect your business data. Thus avoid any kind of cyber threats or data leaks. Typically, it covers the protection of corporate hardware and software – from users’ devices to cloud resources.
Having a reliable and secure IT infrastructure could help your business get rid of potential issues such as
- data breaches and their costly consequences,
- harmful malware disrupting your operations and compromising your data,
- system failures and downtime,
- financial losses due to stolen data, ransom payments, and recovery costs,
- penalties for not following strict data protection regulations.
Benefits of Robust Infrastructure Security
The more your company relies on technology and mass data to run it, the more it becomes vulnerable to cybercrime. It’s estimated that cybercriminals will steal more than 33 billion records by 2023. This is why businesses need to find ways to improve their IT infrastructure protection.
Securing cloud infrastructure is crucial to avoid any form of assault on your tech assets and data. It also helps limit the amount of damage in the case of a successful cyberattack and preserve resilience in cyber security.
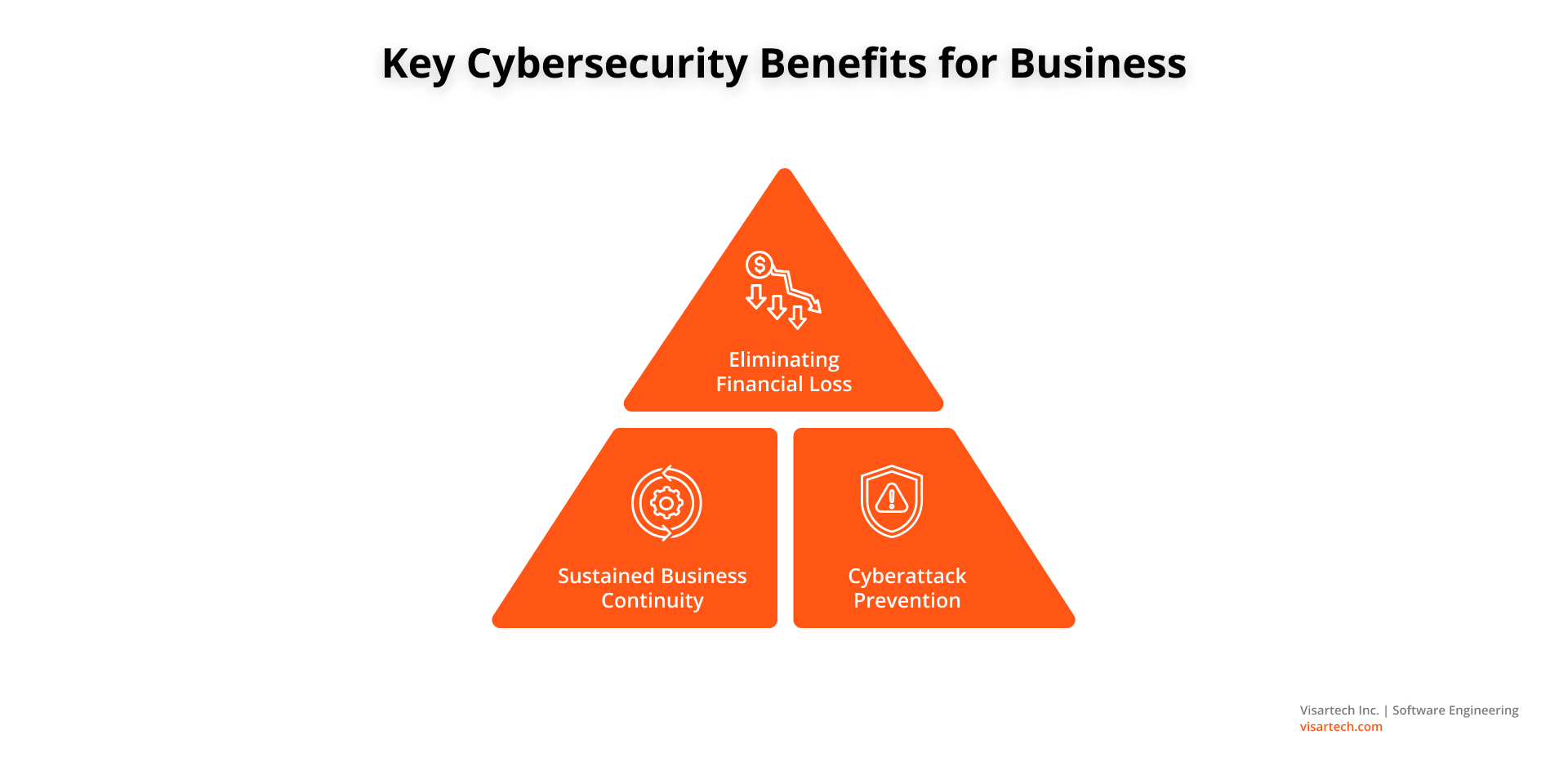
Among the numerous advantages that cybersecurity brings to businesses, notable ones include:
Eliminating Financial Loss
Cyber resilience lowers the financial risk associated with hefty fines. Infrastructure cyber security also safeguards data from being stolen or otherwise corrupted.
The second benefit is that it upholds legal requirements that customer data be protected from cyberattacks. This is crucial as privacy legislation continues to grow.
Sustained Business Continuity
Robust IT infrastructure security lessens the likelihood of damage caused by careless users. Cyber resilience protects your organization by eliminating threats before they do any damage. This also greatly reduces the number of cyber incidents.
The majority of malware does not enter a business network on purpose by an inside user. Rather, it enters via an unintentional click on a link or email attachment. The cybersecurity practices we’ve discussed can reduce such risks to your business continuity. Especially, when these errors are unavoidable.
Cyberattack Prevention
An expert approach to cybersecurity shields all your company’s technological assets from attacks. IT infrastructure security, thus, serves as the first line of protection for the majority of businesses. It protects them from malware and other forms of vulnerabilities.
Infrastructure security aims to protect your network’s users and their sensitive data against attack. It also maintains hardware and software security on the network.
Main Levels of IT Infrastructure Security
Can you imagine that a cyberattack happens once every 39 seconds? In fact, more than 2000 cyberattacks are launched daily against internet-connected, unprotected systems.
Before, we talked about ways to optimize your technology infrastructure using the cloud and DevOps strategies. An essential step in this process is infrastructure security management. It often requires the use of key hardware and software assets. They include consumer devices, data center resources, cloud resources, and networking infrastructure.
Read more: Budget-Saving Strategies to Optimize Your IT Infrastructure
Discover the best DevOps practices that help to reduce IT infrastructure costs
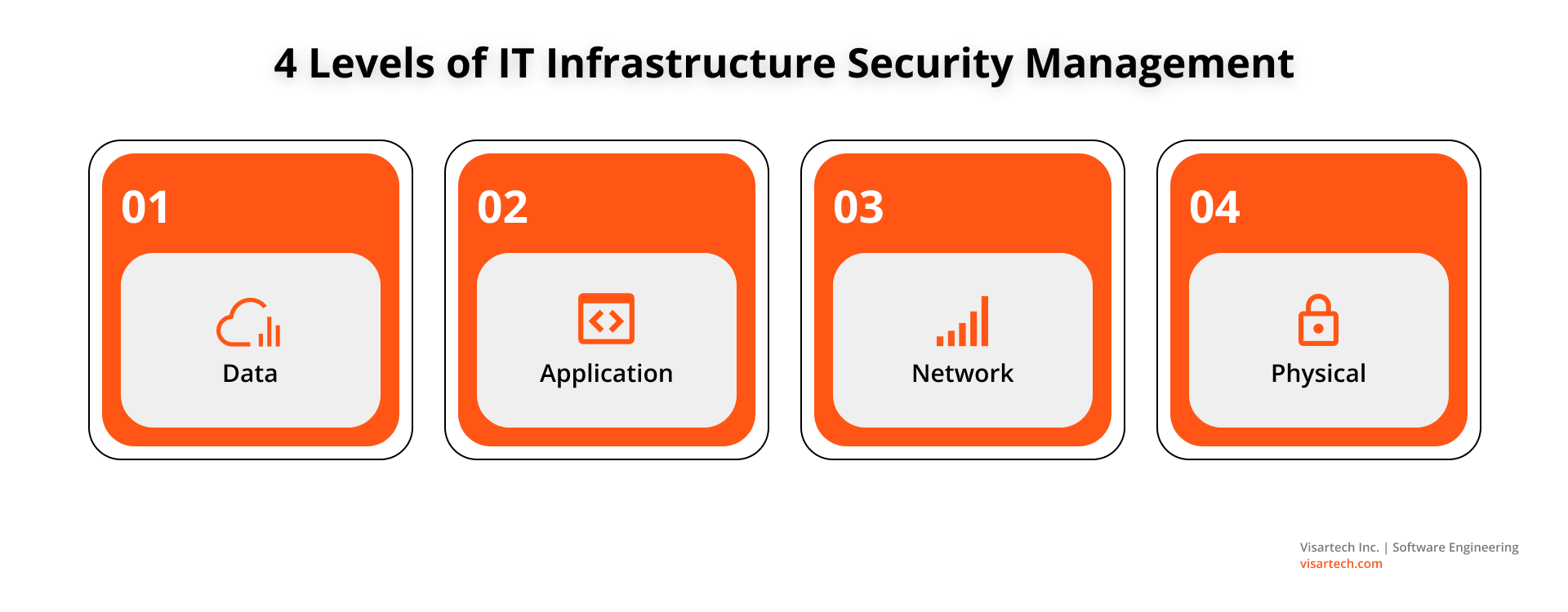
CIOs rank cybersecurity above more strategic IT investments like the cloud or AI. They use several strategies to protect their devices and systems from both physical and digital threats. Typically, there are four tiers for managing IT infrastructure security:
#1. Data
The more data you have, the harder it is to secure it across your corporate network. This means more endpoints to keep an eye on.
Enterprise endpoint cyber security tools include:
- URL filtering;
- Antivirus programs;
- Sandboxing;
- Secure email gateways (SEGs);
- Endpoint detection and response tools (EDRs).
Another effective strategy is encoding data to restrict access to only authorized individuals. Additionally, data encryption, backups, and anonymization techniques are all part of data security.
#2. Application
Security at the application level involves safeguarding databases from incidents like SQL injections. This also means fortifying other programs against unauthorized access or harmful activity.
Hackers can enter your IT system through flaws in outdated software. Patching is one good method to address this problem. It guarantees your software and firmware upgrades are distributed throughout a corporate network. The strategy deals with security gaps and offers extra functionality. Patching also improves performance and fixes bugs for corporate applications.
#3. Network
A firewall is frequently the primary defense mechanism in terms of corporate network security. It creates a barrier between the secure network of your business and the suspicious ones (e.g., open Wi-Fi).
The protection of data as it enters, leaves, and moves within the network is the main goal of network security. This involves identity and authorization systems, effective firewall management, and traffic encryption. It can be on-premises or in the cloud (in this case, we deal with cloud security).
IT infrastructure security policies are crucial for network security. They define the network traffic that can access trusted network resources. You can manage it by controlling inbound and outgoing network traffic. Also, multi-factor authentication (MFA) safeguards your network. It requires two (or more) forms of verification before allowing the use of network resources.
#4. Physical
Physical security is just as important as cybersecurity. Your IT infrastructure needs to be physically protected. This includes things like fences, security cameras, backup generators, and closed doors. Failure prevention techniques are also a part of physical security. This step involves placing backup equipment in a different region of the world.
Cybersecurity doesn’t shield your digital assets against physical theft. Or even vandalism and natural catastrophes. Thus, a physical security plan should include data recovery procedures. And it’s recommended that they use offsite backups situated in several geographical regions.
10 Best Practices for IT Infrastructure Security
Just think about it: the cost of cybercrime will hit $10.5 trillion by 2025, as per the “2022 Cybersecurity Almanac”. Adopting cybersecurity practices today will save your business from such a financial loss in the future.
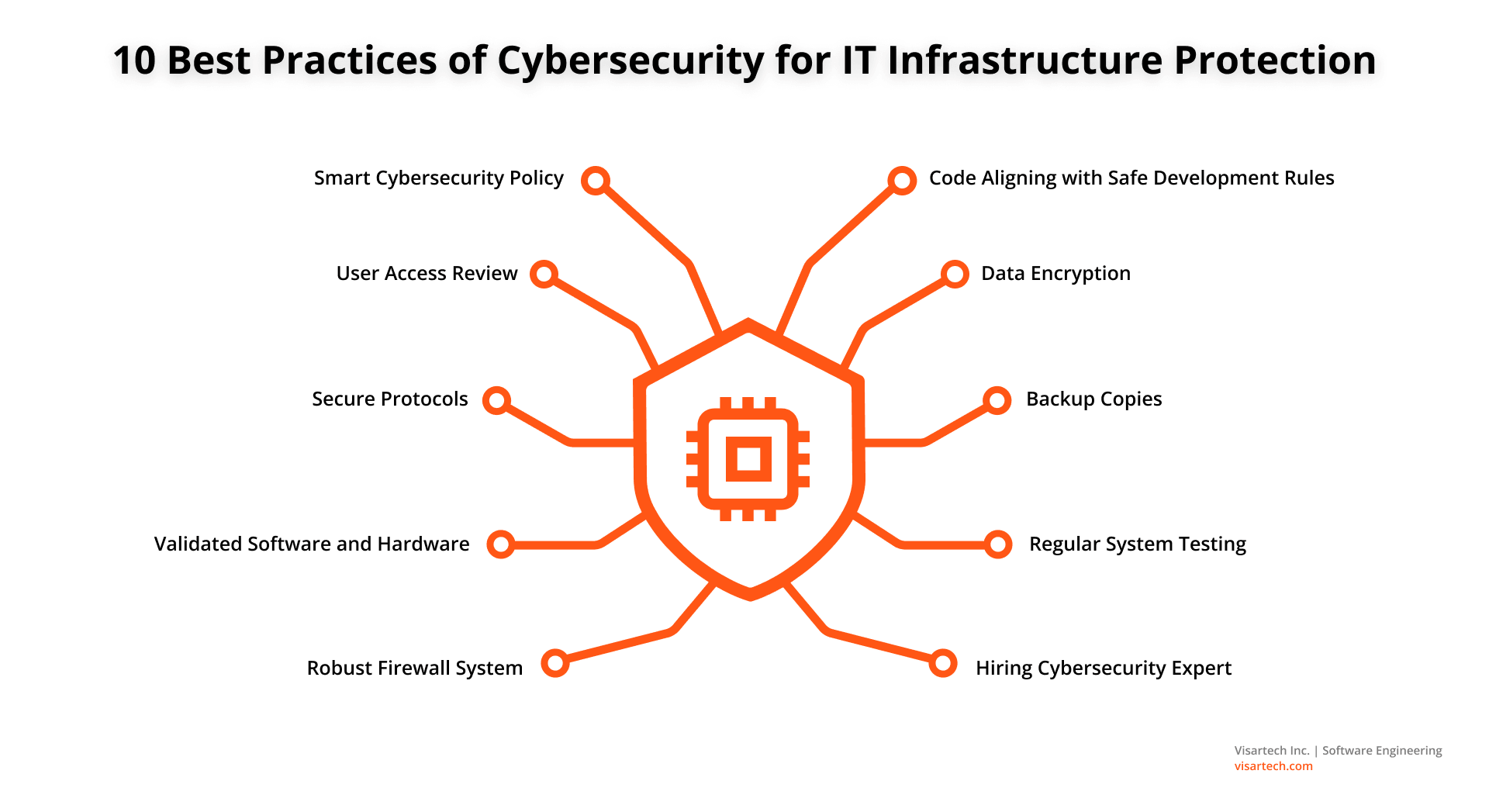
Here are the top ten practices to enhance your server and infrastructure security strategy in business:
#1. Smart Cybersecurity Policy
Understanding and addressing all the hazards is crucial for cyber security management. Establishing security standards should be your first step. They must be relevant to your company’s operations, your niche, and the skills of your personnel.
You should also clearly define the regulations for employee and administrative access to your systems. These include passwords, other end-user credentials, and content-filtering procedures. This will put IT infrastructure security policies in place.
Password security should be taken very seriously. Create strong passwords for every login and use two-factor authentication. Also, specify who handles what while handling cyber risks.
#2. User Access Review
Regularly check user permissions. Remove those that are no longer required, as well as any that are granted to users who leave the company to prevent unauthorized access. It’s best to use privileged access and access management technologies to limit the number of users who can obtain information.
Additionally, one of the greatest practices for network security is efficient password management. The rule is as follows: at least 10 characters in a password and periodical updates. You can use systems for managing passwords or include multi-factor authentication.
#3. Secure Protocols
Security protocols rely on the cryptography technique. This helps them protect sensitive data, financial data, and file transmission. They provide information on the data structure and data representation, as well as how the algorithm functions.
Make sure your web assets are using secure protocols. For example, Safe Socket Layer (SSL) and Secure Shell (SSH) offer a secure path for communication even across unsecured networks.
#4. Validated Software and Hardware
Choosing hardware and software, available at a price or even free, is really attractive. But making such a decision has certain unspoken dangers. You may select solutions that already have an efficient security mechanism built in. Yet this usually comes at a cost.
Besides, it’s crucial to refrain from obtaining software from unreliable sites. They could include malicious software in them. It can infiltrate your system and provide others with access to the private information of your enterprise.
#5. Robust Firewall System
A key component of any cybersecurity strategy should include firewalls. Make sure they are set up correctly because a poorly set firewall poses just as much risk as none at all.
Yet, a lot of businesses struggle with network-level firewall installation. Each employee’s gadget must have a firewall, but the overall systems should also be secured. Thus, it is strongly advised to set up hardware and packet-filtering firewalls. They add another layer of network infrastructure security.
#6. Code Aligning with Safe Development Rules
A framework like DevSecOps might be helpful for protecting your technological infrastructure. It can establish a security-focused attitude within the development team. Ensure the code complies to secure development principles.
#7. Data Encryption
Whenever possible, rely on data encryption. For hackers who successfully breach the system but lack the keys, encrypted files are generally worthless.
IT firms must regularly test data categorization and use encryption where necessary. Besides, VPNs can add another degree of cybersecurity. This concerns your employees who may need to access sensitive information from faraway locations.
#8. Backup Copies
Back up all your systems on a regular basis. Offsite backups are your best line of security against ransomware assaults. Back up both highly sensitive and operationally significant data. This is essential when dealing with cybercrime.
#9. Regular System Testing
Conduct frequent system stress tests for the ultimate security resilience in your organization. To find vulnerabilities, conduct security scans and penetration testing.
#10. Hiring Cybersecurity Expert
Even the finest practices for IT infrastructure protection might not always help. Companies still struggle to manage their time and resources to set cybersecurity in motion. Working with a cybersecurity specialist can help you avoid this hazard.
Our Visartech team can protect your crucial IT infrastructure. By integrating and managing cybersecurity technologies and procedures, we provide key cybersecurity services. They include:
- Company security architecture review;
- Threat intelligence;
- Detection and response capability development.
With the help of these services, our team maps out your current threat environment. Your company is, therefore, constantly informed of the key insights about any potential cyber threat.
Read also: Behind the Scenes of Development Process: The Visartech Workflow
Learn the methods of organizing effective workflow that we apply at Visartech
How to Build a Secure IT Infrastructure for Your Business?
Companies start recognizing the threat that poor cybersecurity strategy represents to their business. More specifically, their productivity, goodwill, and bottom line. If you want to be genuinely safe, you need a clear plan for how to handle any future security needs.
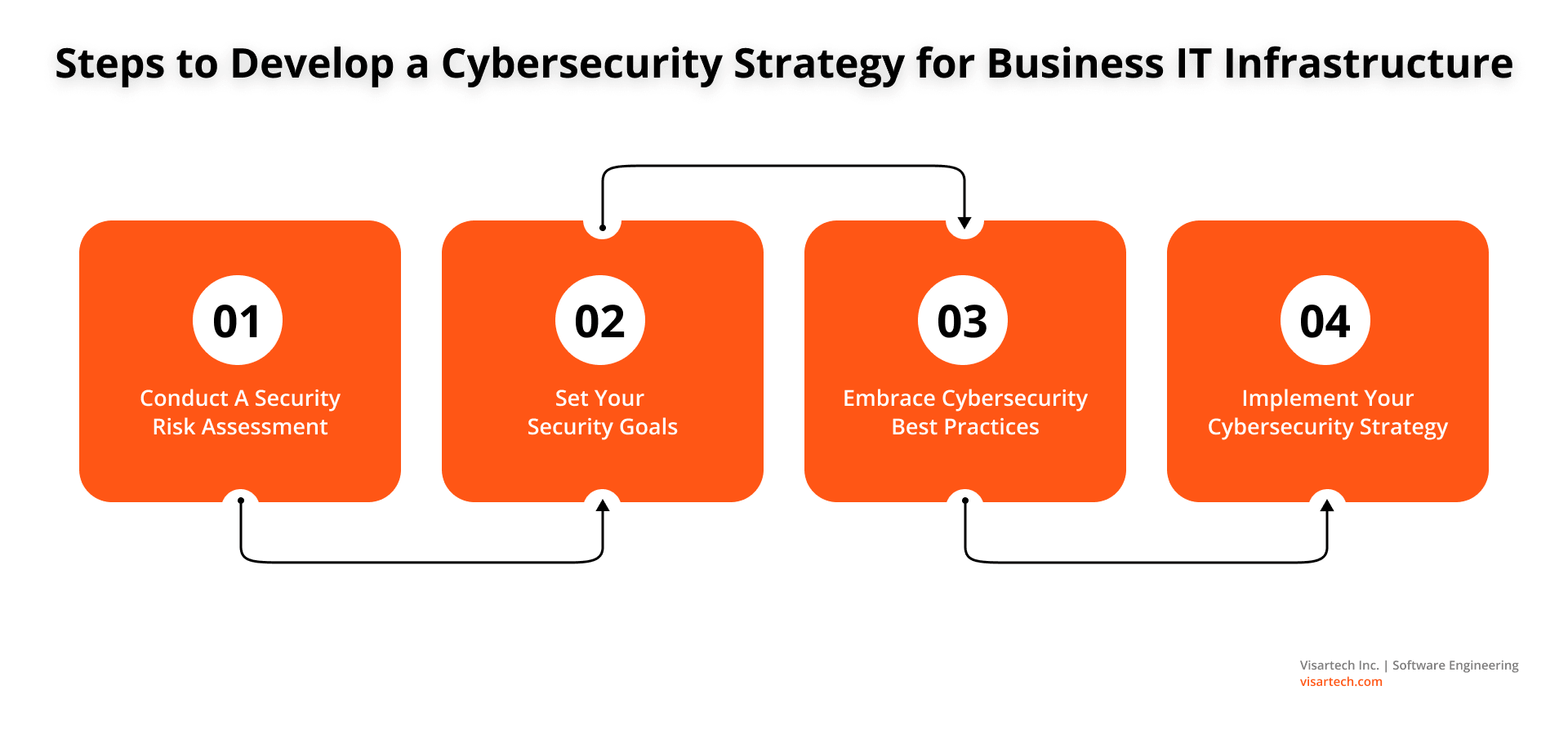
These steps will strengthen your cybersecurity strategy:
Conduct A Security Risk Assessment
Security risk assessment is carried out to evaluate, analyze, and improve your company’s cyber resilience. This process involves cooperation from many groups and data owners. The management’s commitment helps allot resources and execute the necessary cybersecurity solutions.
The value of different data created and kept within the company is likewise determined by cyber risk management. Thus, allocating tech resources where they are most required would be impossible without this step. Your management team must perform an IT infrastructure audit to determine the data sources that are most important to the firm. This can also indicate where the storage is situated and data vulnerabilities to properly assess risk.
Set Your Security Goals
Business goals must be aligned with your cybersecurity strategy. This is a golden role for success in critical infrastructure protection. Once your corporate goals are clear, it’s easier to start integrating the cybersecurity framework into it.
Focusing on different areas might help in developing security goals:
- Establish reasonable expectations;
- Assess your security maturity;
- Comprehend your company’s risk appetite;
- Take immediate action on simple tasks;
- Deal with security issues as they arise.
Embrace Cybersecurity Best Practices
Cybercriminals use cutting-edge tactics to attack modern businesses. This includes companies of all sizes, geographies, and industrial sectors. So, you must have a solid plan for managing physical and cybersecurity across crucial systems and assets. This will help you operate in the present business climate.
The cybersecurity practices mentioned above will help protect your crucial technology infrastructure. As a result, your team can enhance its cyber security resilience. It will also prevent malevolent behavior of any sort that can threaten your information system resources.
Implement Your Cybersecurity Strategy
The strategy assessments and policy plans are almost finished. This is the time to allocate tasks to teams and prioritize remedial efforts. To internal teams, assign cybersecurity tasks according to their priority. Also, make use of the Project Management team inside your company, if one exists. Provide leadership, interact with the internal teams, and plan the activities if there is no project team available. Set realistic deadlines: it’s best to plan for more time than you think.
Cybersecurity will be much more efficient and qualitative with a reliable vendor. There are now a dizzying array of options as a result of the rising demand for strong security protection. Visartech can be your skilled tech consultant for IT infrastructure security as you navigate this niche.
Final Thoughts on IT Infrastructure Security
Securing your organization starts with securing your infrastructure first. Stable and secure IT infrastructure accounts for business resilience and budget saving. Businesses need a cyber security and IT infrastructure protection solution that guarantees continuous availability. Adopting the practices that we have discussed in this article can help them achieve this goal.
Cybersecurity should not be a nerve-racking experience for your business. These practices are constantly evolving, but we have listed a few tried and true methods that every company should use. Cybersecurity is all about staying one step ahead of the hackers. That’s why you should keep your systems up-to-date and continuously watch for vulnerabilities.